We tend to associate free with good. That’s not the case though when what is free is unauthorized root-level access to your Linux systems! On January 26, 2021, a vulnerability, CVE-2021-3156, was disclosed that affects just about every Linux or Unix distribution that utilizes the sudo functionality.
TLDR: You need to update your operating system as soon as possible to ensure you have the patch.
Now that you have scheduled emergency patching windows for all your impacted systems . . . you did right? Let’s get into how this vulnerability works and what the potential impact is.
On a healthy system, you have to run a su command and provide the root password or have your account authorized in the /etc/sudoers file to gain administrative level access to a Linux system. The Baron Samedit bug, however, utilizes a buffer overflow in the Sudo logic to allow a non-privileged account to bypass this security mechanism and run commands with root-level privileges.
While running a sudo command in shell mode (either with the -s or -i argument), special characters must be escaped with a backslash / character. With this vulnerability, however, you can add an extra backslash to a any command. This will cause sudo to skip the policy review step where it reads /etc/sudoers to ensure the executing account has sudo privileges. Now with ill-gotten access to root-level privileges, a bad actor could do anything to a compromised system.
You can test this for yourself by logging into a Linux system with a non-privledged account and running:
$ sudoedit -s /If the prompt returns sudoedit: your system is vulnerable and needs to be patched. However, if your system returns a usage description, your system has been patched and is no longer susceptible to this attack.
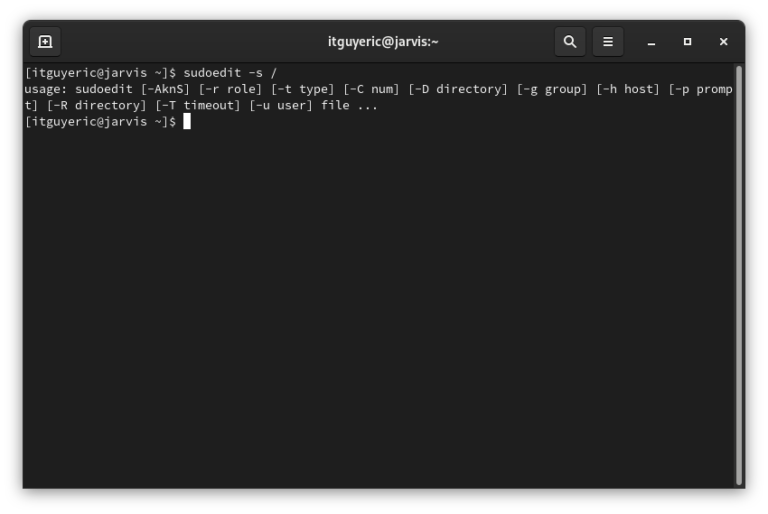
This vulnerability was discovered by independent testing by Qualys Inc. an information security and compliance company. Their research found that Baron Samedit was actually introduced in version 1.8.2 released, get this, 10 years ago! This bug has been in the wild for almost a decade! It impacts legacy versions 1.8.2 through 1.8.31p2. The vulnerability is also present in current supported version 1.9.0 through 1.9.5p1.
Rarely do we see a bug with such a wide pool of targets. Sudo is utilized in Unix and Linux systems everywhere. This impacts popular distributions like Red Hat Enterprise Linux, Ubuntu, Debian, SUSE, Fedora, and so on. Even BSD and other Unix derivatives are not immune to CVE-2021-3145. The risk of any bad actor gaining root-level rights to your systems cannot be overstated. Once running as root, your system can become slave to botnets, used for crypto-mining, or exploited to retrieve sensitive data.
| Distribution | Fixed Version | More Details |
|---|---|---|
| Red Hat Enterprise Linux 8 | 1.8.29-6.el8_3.1 | Advisory |
| Ubuntu 20.04 | 1.8.31-1ubuntu1.2 | Advisory |
| SUSE Enterprise Linux 15 | 1.8.22-4.15.1 | Advisory |
| openSUSE Leap 15.2 | 1.8.22-lp152.8.6.1 | Advisory |
| Fedora 33 | 1.9.5p2-1.fc33 | Advisory |
| Debian 10 | 1.8.27-1+deb10u3 | Advisory |
| Arch Linux | 1.9.5.p2-1 | Advisory |
| Gentoo | 1.9.5.p2 | Advisory |
If you would like to read more about Baron Samedit and the deeper, technical explanation of how this vulnerability was found and how it works, Qualys published an in-depth blog on their findings: CVE-2021-3156: Heap-Based Buffer Overflow in Sudo
You maybe wondering the same thing I was . . . Where in the world did Qualys get the name Baron Samedit? Turns out, its a play on sudoedit and Baron Samedi. According to Voodoo mythology, Baron Samedi is the Loa (god) of the Dead. He is a chaotic spirit who spends his time smoking, drinking, and well possessing others. This ‘spirit’ even attempts to ensnare everyone’s favorite secret agent, James Bond.
Just like 007, we need to overcome this new foe, Baron Samedit. Patch your systems. You can also check out the other Security related topics here on Front Page Linux if you’d like some more info to better secure you system.
—
Additional Reading:
CVE.Mitre.Org: 2021-3156
Sudo.ws: Buffer overflow in command line unescaping
ZDNet: 10-year-old Sudo Bug lets Linux users gain root-level access









It’s a good thing to stumble upon that kind of article but as a rather newbie it’s always a disappointment to not find in the article any info on how you check the sudo version or update I know it’s basic info and most of the audience here don’t need that. I kind of guess what I have to do but a 3 lines reminder wouldn’t hurt.
I know it’s basic info and most of the audience here don’t need that. I kind of guess what I have to do but a 3 lines reminder wouldn’t hurt.
I found the infos elsewhere and the thing now is when I try to update terminal is telling me sudo is already the latest version (1.9.1-1ubuntu1.1) but in the article the recommended version is sudo-1.9.5p2
(Pop OS 20.10)
I’m running a LinuxLite distro atm on a vm, and it seems that it’s patched. Did you run the latest updates for your distro? It should be fixed by now.
It’s unfortunate that it took about 10 years to get fixed, but better late then never i suppose.
I think it is telling you that because it is the latest version in your versions repository. I would hope that you will see an update very soon.
You raise a good point about mentioning how to check for current version. I will keep that in mind in future articles. Thank you for the feedback.
Well that was a nice snarky reply
First thing I tried was sudo update but as nothing was updating I wondered how to check sudo version, which bring us to my reply here.
I could have gone to Pop os forum but I saw the article here and this forum is generally welcoming
Join the discussion at forum.tuxdigital.com
7 more replies